802.1X is an IEEE Standard for port-based Network Access Control (PNAC). It is part of the IEEE 802.1 group of networking protocols and provides an authentication mechanism to devices wishing to attach to a LAN or WLAN.
802.1X authentication involves three main components:
1. Supplicant - The client device that wishes to be authenticated and gain access to the network. This could be a workstation, a smartphone, a printer, etc.
2. Authenticator - Typically a network switch or wireless access point that acts as an intermediary between the supplicant and the authentication server. The authenticator controls the physical access to the network based on the authentication status of the supplicant.
3. Authentication Server - Usually a RADIUS (Remote Authentication Dial-In User Service) server that checks the credentials of the supplicant and informs the authenticator whether or not the supplicant should be allowed access to the network.
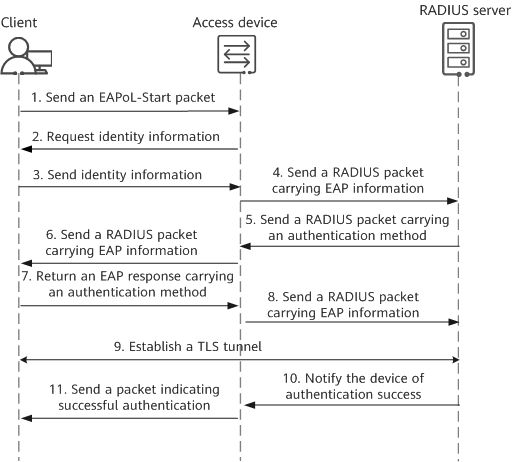
1. When a client device (supplicant) connects to a network using a switch or access point (authenticator), the authenticator creates a new port for the connection but keeps it in an unauthorized state, which blocks all traffic except for 802.1X authentication traffic.
2. The supplicant sends an EAP (Extensible Authentication Protocol) start message, which initiates the authentication process and is passed by the authenticator to the authentication server.
3. The authentication server challenges the supplicant to prove its identity. This could involve a password, a digital certificate, or other means of identification depending on the specific EAP method being used.
4. The supplicant sends the appropriate credentials back through the authenticator to the authentication server.
5. If the authentication server verifies the credentials, it sends a success message back to the authenticator. The authenticator then changes the state of the port to authorized, allowing the supplicant to access the network.
6. If the authentication fails, the port remains in the unauthorized state, and network access is denied.
802.1X provides a robust framework for network access control, particularly useful in Wi-Fi networks where users and devices are highly mobile and the network might otherwise be open to unauthorized access. It is also used to implement various types of network policies, such as VLAN assignments, quality of service (QoS), and other access restrictions based on user or device identity.